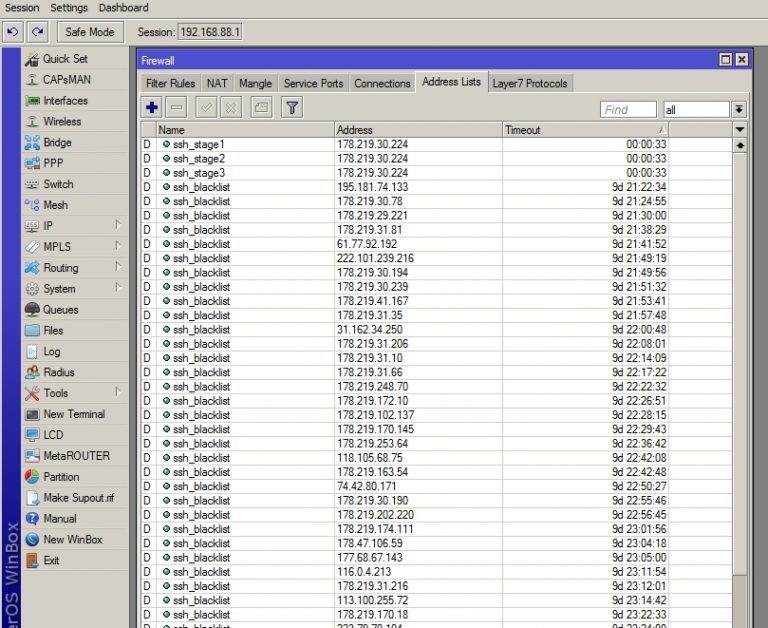
Данная цепочка подходит тем, кто не хочет менять стандартный порт SSH и нуждается в доступе с любого ip-адреса.
Если вы не хотите или не можете поменять стандартные номера портов для доступа к микротику по протоколам telnet, ssh и winbox, но вам нужен к нему доступ с разных заранее неизвестных подсетей предлагаю следующее решение.
Данная цепочка правил работает так: если в течение минуты с одного IP производится более 3х попыток входа — данный IP блокируется на 10 дней. Для winbox дается 5 попыток.
Первое правило разместите над запрещающим input правилом. Остальные — неважно куда, на них будет произведён jump
/ip firewall filter
add action=jump chain=input comment="sshbruteforces chain" connection-state=new dst-port=22 jump-target=sshbruteforces protocol=tcp
add action=drop chain=sshbruteforces comment="drop ssh brute forcers" src-address-list=ssh_blacklist
add action=add-src-to-address-list address-list=ssh_blacklist address-list-timeout=1w3d chain=sshbruteforces connection-state=new src-address-list=ssh_stage3
add action=add-src-to-address-list address-list=ssh_stage3 address-list-timeout=1m chain=sshbruteforces connection-state=new src-address-list=ssh_stage2
add action=add-src-to-address-list address-list=ssh_stage2 address-list-timeout=1m chain=sshbruteforces connection-state=new src-address-list=ssh_stage1
add action=add-src-to-address-list address-list=ssh_stage1 address-list-timeout=1m chain=sshbruteforces connection-state=new
add chain=sshbruteforces dst-port=22 protocol=tcp
add action=drop chain=forward comment="drop ssh brute downstream" disabled=no dst-port=22 protocol=tcp src-address-list=ssh_blacklist
add chain=sshbruteforces dst-port=22 protocol=tcp connection-state=new
add action=drop chain=forward comment="drop ssh brute downstream" dst-port=22 protocol=tcp src-address-list=ssh_blacklist
add action=jump chain=input comment="telnetbruteforces chain" connection-state=new dst-port=23 jump-target=telnetbruteforces protocol=tcp
add action=drop chain=telnetbruteforces comment="drop telnet brute forcers" src-address-list=telnet_blacklist
add action=add-src-to-address-list address-list=telnet_blacklist address-list-timeout=1w3d chain=telnetbruteforces connection-state=new src-address-list=telnet_stage3
add action=add-src-to-address-list address-list=telnet_stage3 address-list-timeout=1m chain=telnetbruteforces connection-state=new src-address-list=telnet_stage2
add action=add-src-to-address-list address-list=telnet_stage2 address-list-timeout=1m chain=telnetbruteforces connection-state=new src-address-list=telnet_stage1
add action=add-src-to-address-list address-list=telnet_stage1 address-list-timeout=1m chain=telnetbruteforces connection-state=new
add chain=telnetbruteforces dst-port=23 protocol=tcp
add action=drop chain=forward comment="drop telnet brute downstream" disabled=no dst-port=23 protocol=tcp src-address-list=telnet_blacklist
add chain=telnetbruteforces dst-port=23 protocol=tcp connection-state=new
add action=drop chain=forward comment="drop telnet brute downstream" dst-port=23 protocol=tcp src-address-list=telnet_blacklist
add action=jump chain=input comment="winboxbruteforces chain" connection-state=new dst-port=8291 jump-target=winboxbruteforces protocol=tcp
add action=drop chain=winboxbruteforces comment="drop winbox brute forcers" src-address-list=winbox_blacklist
add action=add-src-to-address-list address-list=winbox_blacklist address-list-timeout=1w3d chain=winboxbruteforces connection-state=new src-address-list=winbox_stage5
add action=add-src-to-address-list address-list=winbox_stage5 address-list-timeout=1m chain=winboxbruteforces connection-state=new src-address-list=winbox_stage4
add action=add-src-to-address-list address-list=winbox_stage4 address-list-timeout=1m chain=winboxbruteforces connection-state=new src-address-list=winbox_stage3
add action=add-src-to-address-list address-list=winbox_stage3 address-list-timeout=1m chain=winboxbruteforces connection-state=new src-address-list=winbox_stage2
add action=add-src-to-address-list address-list=winbox_stage2 address-list-timeout=1m chain=winboxbruteforces connection-state=new src-address-list=winbox_stage1
add action=add-src-to-address-list address-list=winbox_stage1 address-list-timeout=1m chain=winboxbruteforces connection-state=new
add chain=winboxbruteforces dst-port=8291 protocol=tcp
add action=drop chain=forward comment="drop winbox brute downstream" disabled=no dst-port=8291 protocol=tcp src-address-list=winbox_blacklist
add chain=winboxbruteforces dst-port=8291 protocol=tcp connection-state=new
add action=drop chain=forward comment="drop winbox brute downstream" dst-port=8291 protocol=tcp src-address-list=winbox_blacklist
На всякий случай переключение в терминале Ctrl+V